Here's a pretty simple dd in ANSI C.
I am really planning do more with it, like the dd for linux!
Code (Very much simplistic)
Example:
Output:
Download the full code here!
Enjoy!
Monday, April 30, 2012
Sunday, April 29, 2012
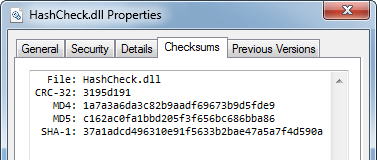
My md5sum
This is a little example of a md5 sum application, using the Hash lib.
Get a md5 sum of a entire device, here's a screenshoot.
Download Source
Enjoy!
Get a md5 sum of a entire device, here's a screenshoot.
Download Source
Enjoy!
HashLib 0.1
Here's the new version of the Hash Lib, still compatible with windows, linux, and mac!
The new features added were:
- Correct some minor bugs;
- Now you can get a hash of a file, with every algoritm! (Support large files!)
Download Source
Example:
The new features added were:
- Correct some minor bugs;
- Now you can get a hash of a file, with every algoritm! (Support large files!)
Download Source
Example:
Monday, April 23, 2012
File Checksum Integrity Verifier
It's rare when i post something that isn't from my authority but there is always an exception to the rule.
fciv.exe c:\mydir\myfile.dll
fciv.exe c:\ -r -exc exceptions.txt -sha1 -xml dbsha.xml
fciv.exe c:\mydir -type *.exe
fciv.exe c:\mydir -wp -both -xml db.xml
fciv.exe -add %systemroot% -r -XML c:\temp\windows-hashes.XML
To list the contents of the database to the console, type the following command:
fciv.exe -list -XML c:\temp\windows-hashes.XML
To verify the contents of the XML database against the current file system files, type the following command:
fciv -v -XML c:\temp\windows-hashes.XML
The File Checksum Integrity Verifier (FCIV) is a command-prompt utility that computes and verifies cryptographic hash values of files. FCIV can compute MD5 or SHA-1 cryptographic hash values. These values can be displayed on the screen or saved in an XML file database for later use and verification.
Which is very nice!
Some examples:
fciv.exe c:\ -r -exc exceptions.txt -sha1 -xml dbsha.xml
fciv.exe c:\mydir -type *.exe
fciv.exe c:\mydir -wp -both -xml db.xml
More useful one;
To create the database and to save it to the C:\Temp directory, type the following command:
To list the contents of the database to the console, type the following command:
fciv.exe -list -XML c:\temp\windows-hashes.XML
To verify the contents of the XML database against the current file system files, type the following command:
fciv -v -XML c:\temp\windows-hashes.XML
The application can be found here.
Monday, April 16, 2012
HashLib
Here's my new Hash Lib, built again in Ansi C OOP. The lib is compatible with windows, linux, and mac too!
Every hash algorithm has a little cosmetic change, just to uniform all hash algorithm implementations. It doesn't have all hash algoritms, but i think that it has all the most important ones.
Download Source
Example:
Sunday, April 1, 2012
PEFile Lib
Here's my new PEFile Lib, is propose is just read PE files only, is written in OOP C which is really nice.
It doesn't support PE based on 64 bits architecture, yet! (tomorrow)
Download Source
Little example to show how it works. You could import the lib our just copy/paste into your project.
It doesn't support PE based on 64 bits architecture, yet! (tomorrow)
Download Source
Little example to show how it works. You could import the lib our just copy/paste into your project.
Friday, March 2, 2012
Monday, February 20, 2012
Sunday, February 19, 2012
Chrome Link Spoof
Here are more than twenty ways to spoof a link in Google Chrome:
There is more, but i think is enough! :)
(Tested with Google Chrome 17.0.963.46)
Enjoy!
There is more, but i think is enough! :)
(Tested with Google Chrome 17.0.963.46)
Enjoy!
Saturday, February 11, 2012
Sunday, January 22, 2012
Get Kernel32 Base Address 2.0
[1.0]
xor ebx, ebx // clear ebx
mov ebx, fs:[ 0x30 ] // get a pointer to the PEB
mov ebx, [ ebx + 0x0C ] // get PEB->Ldr
mov ebx, [ ebx + 0x14 ] // get PEB->Ldr.InInitializationOrderModuleList.Flink (1st entry)
mov ebx, [ ebx ] // get the next entry (2nd entry)
mov ebx, [ ebx ] // get the next entry (3rd entry)
mov ebx, [ ebx + 0x10 ] // get the 3rd entries base address (kernel32.dll)
From : http://hi.baidu.com/heartdbg/blog/item/c1f16fdd4a7f88e677c63858.html
21 bytes, use only one register, ebx.
Dump:
Hex dump Command
---------------------------------------------
33DB XOR EBX,EBX
64:8B1D 300000 MOV EBX,DWORD PTR FS:[30]
8B5B 0C MOV EBX,DWORD PTR DS:[EBX+0C]
8B5B 14 MOV EBX,DWORD PTR DS:[EBX+14]
8B1B MOV EBX,DWORD PTR DS:[EBX]
8B1B MOV EBX,DWORD PTR DS:[EBX]
8B5B 10 MOV EBX,DWORD PTR DS:[EBX+10]
[2.0]
xor eax, eax
mov eax, fs:[ eax + 30h ] // get PEB pointer
mov eax, [ eax + 0x0C ] // get PEB->Ldr
mov esi, [ eax + 0x14 ] // get PEB->Ldr.InMemoryOrderModuleList.Flink (1st entry)
lodsd // get the next entry (2nd entry)
xchg esi, eax
lodsd // get the next entry (3rd entry)
mov eax, [ eax + 0x10 ] // get the 3rd entries base address (kernel32.dll)
18 bytes, use two registers, eax, esi, and it's null-free.
Dump:
Hex dump Command
--------------------------------------------
33C0 XOR EAX,EAX
64:8B40 30 MOV EAX,DWORD PTR FS:[EAX+30]
8B40 0C MOV EAX,DWORD PTR DS:[EAX+0C]
8B70 14 MOV ESI,DWORD PTR DS:[EAX+14]
AD LODS DWORD PTR DS:[ESI]
96 XCHG EAX,ESI
AD LODS DWORD PTR DS:[ESI]
8B40 10 MOV EAX,DWORD PTR DS:[EAX+10]
Saturday, January 21, 2012
MASM String Instructions
The x86-64 processor has a number of instructions that provide the programmer with the ability to manipulate strings at a byte, word, double and quadruple word length. These instructions are, stosx, movsx, cmpsx. lodsx and scasx, and can be combined with conditional repeat mnemonics, these are rep, repe, repne, repz, and repnz, and they are convenient because they let you avoid writing lots of little loops, which can make the code really bad for the readers . The “x” represent the size of the basic unit, these units are b, byte, w word, d doubleword, and q quadword respectively.
The main goal of this paper is to provide some knowledge about string manipulation, without using the common instruction set.
Tuesday, January 10, 2012
Wednesday, January 4, 2012
Subscribe to:
Posts (Atom)